Protecting Local Government Data: Preventing Sensitive Data Leakage into AI Systems with VDI
How Virtual Desktops Safeguard County Data from Unintended Exposure to AI Tools and Cyber Threats
For local government IT leaders such as CIOs, CISOs, and IT Directors, the proliferation of AI tools presents new challenges in data security. Employees may inadvertently input sensitive information into unauthorized AI applications, leading to potential data breaches and compliance violations. Traditional VPN solutions, offering broad network access, often lack the necessary controls to prevent such incidents. Virtual Desktop Infrastructure (VDI) provides a robust solution by containing data within secure environments, reducing the risk of unintended exposure to AI systems.
The Challenge: Unintended Data Exposure to AI Tools
The rise of AI applications in the workplace has led to scenarios where employees, seeking efficiency, use AI tools without proper authorization or oversight which is a phenomenon known as "shadow AI." This practice can result in sensitive data being fed into AI systems, which may store or process the information in ways that compromise confidentiality. Such data leakage can occur through misconfigured integrations, inadequate access controls, or lack of employee awareness. Moreover, VPN-based remote access solutions often lack the granular control needed to monitor and restrict data flow to unauthorized applications.
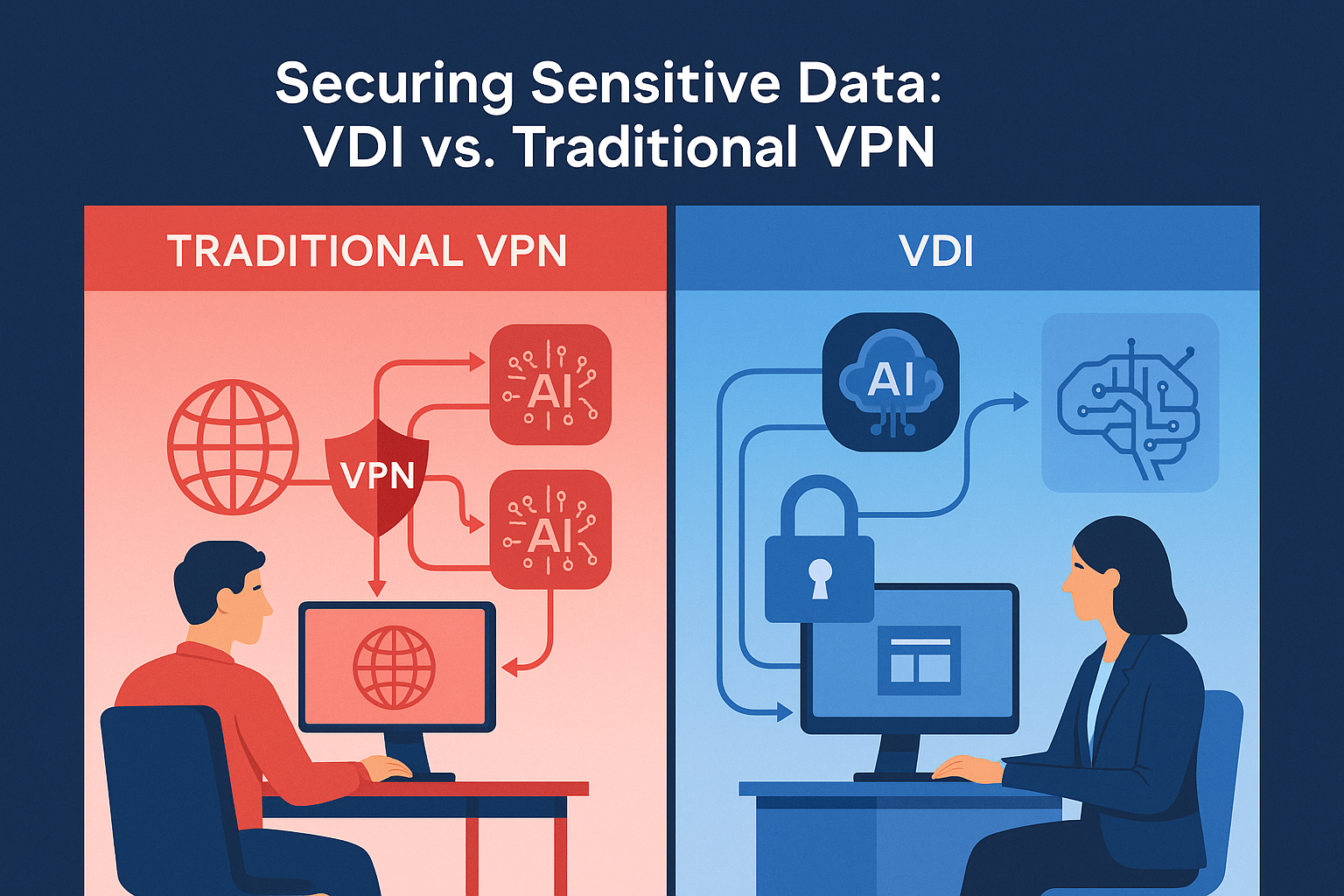
How VDI Mitigates Data Leakage into AI Systems
VDI creates secure, isolated digital environments that prevent sensitive county data from being inadvertently shared with external AI tools. By centralizing data and applications within a controlled infrastructure, VDI ensures that information remains within the organization's security perimeter. This setup allows IT administrators to enforce strict access controls, monitor user activity, and restrict the use of unauthorized applications. Key benefits of adopting VDI include:
- Data Containment: Sensitive information stays within the secure virtual environment, reducing the risk of exposure to external AI systems.
- Enhanced Access Controls: Administrators can define user permissions, limiting access to approved applications and preventing the use of unauthorized AI tools.
- Improved Monitoring: VDI solutions offer robust monitoring capabilities, enabling the detection of unusual activities that may indicate attempts to share data with external applications.
Theoretical Case Study: Securing Data for "Springfield County"
Consider the fictional example of "Springfield County," which manages sensitive citizen data across multiple departments, including public health, tax assessment, law enforcement, and social services. Initially, Springfield County relied heavily on VPN-based remote access solutions, resulting in several incidents where employees inadvertently shared sensitive data with unauthorized AI tools. These incidents not only posed security risks but also threatened compliance with data protection regulations.
To address these challenges, Springfield County adopted a comprehensive VDI strategy, implementing secure virtual desktop environments tailored to each department's needs. By centralizing data and applications within the VDI, the county ensured that sensitive information remained within controlled environments. IT administrators established strict access controls, preventing the installation or use of unauthorized AI applications. Additionally, they implemented monitoring tools to detect and respond to any attempts to circumvent security measures. After implementing VDI, Springfield County reported several measurable improvements:
- Elimination of Unintended Data Sharing: Sensitive data remained fully contained within the VDI, with no further incidents of inadvertent exposure to unauthorized AI tools.
- Enhanced Compliance: The controlled environment simplified compliance with data protection regulations, as all data access and usage could be monitored and audited.
- Increased Employee Awareness: Training programs accompanying the VDI rollout raised employee awareness about the risks of unauthorized AI tools, fostering a culture of security.
The Bottom Line
Transitioning from traditional VPNs to a secure VDI solution significantly enhances a local government's ability to protect sensitive data from unintended exposure to AI systems. By containing data within controlled environments and enforcing strict access controls, VDI mitigates the risks associated with shadow AI and ensures compliance with data protection regulations.
For more insights on digital transformation in regulated industries, follow my latest posts on The Deady Group or contact us for more information.
Share on Socials